From Compliance to Opportunity (Part 2)
Continuing Upstream the Value Chain
By Michael Shea and Nis Jespersen
Continuing a level further up the Value Chain.
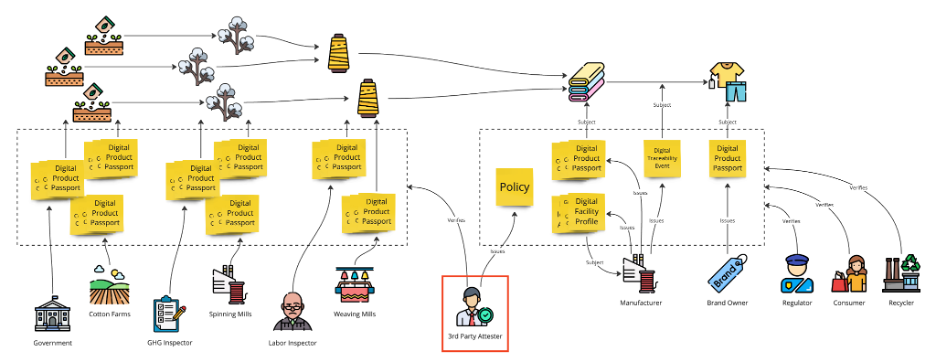
As we expand our clothing value chain example, we might also see that there are two sources of yarn going into the fabric production. For the fabric to be organic, its source yarn must also be. So we see here how Organic Conformity Credentials are provided for both. The result of this is that the product data graph branches out as we go upstream. But while there are quite a few documents in play now, it is still just the same pattern of documents repeating.
Example of an elaborate UNTP Transparency Data Graph, tracing back to the cotton seeds; the graph branches out when there are multiple suppliers.
The UNTP document pattern can be repeated for as long as data is available and for as long as it makes sense to still be associated with the final piece of clothing. Tracing through source cotton fields and onwards to the cotton seeds might be suitable, albeit ambitious. Along the way, the sourcing traceability branches out further, and data gets captured by the same set of UNTP documents.
Material Recycling
Recycled material from one product turns into thread for the next product.
An important mission of digital product passports is to facilitate reuse. Recycling can turn the cotton fibers of our clothing into recycled yarn, which feeds into the value chain of a later clothing product. Since the original piece of clothing was properly documented to be organic, so too can the recycled yarn claimed to be organic. Here, the Recycler verifies the DPP of the reused clothing and issues an Organic Conformity credential linked to the recycled yarn.
Making Sense of a Complex Product Data Graph
We have seen now how a number of digital, verifiable documents are linked. When taken together they form what is referred to as a Transparency Data Graph. But although we understand the intent of the graph’s branches and documents, it is clear that making sense of this kind of data is not a task for humans. Rather, the data graph must be interpreted and “translated” into tangible, actionable indications, for example a consumer’s buying decision or customs agent clearance.
Thankfully, it is relatively trivial for a software application to verify the documents and piece them together to form a data graph of a product’s origin, and various certifications. The verifier will then judge the data graph against a set of rules, which represent the user’s requirements. These rules are called a policy, and define the importance of the various parts of the DPP Data Graph. Often, a deeper graph which goes more steps back into the value chain would be considered more trustworthy and for example score higher on the verifier’s evaluation. Importantly, the policy also defines authoritative issuers of certain kinds of verifiable documents: for example, an organic certificate would only be accepted when issued by an organization on a defined list of accredited organizations.
Policies may differ, for example one consumer may value organic origin higher than another; their choices of trust roots may also vary. The UNTP specification defines the infrastructure on which policies can be defined, but does not define policies (at least not yet). At this point in time, exactly how standardized policies will end up being governed remains to be seen.
Accessing Decentralized Hosted Data
So far we have been glossing over how the Transparency Graph’s many interconnected documents are actually returned to the verifier when the Data Carrier is scanned. Let’s cover this now.
So where does all this data sit? If all the documents were hosted on a single server, all the data carriers could simply be pointed directly to that server. As long as every manufacturer, product producer and brand owner would be happy with having their confidential business information sitting on someone else’s server this would work.
A single monolithic platform is not how the DPP ecosystem has been defined. For both the European Commission ESPR and the UN/CEFACT UNTP the architectural pattern that is required is one of decentralization. Each participant of the value chain is responsible for either hosting their own DPP or hiring a third party to host the DPP on their behalf. For context, when all the delegated acts (8 plus Batteries) are in force by 2029, the volume of DPPs and requests make any architectural pattern other than a decentralized is unfeasible from a performance, resilience, and security context.
Requesting documents hosted decentralized from links returned by the Data Carrier.
Let’s go back to our story to dig a deeper into the architectural model of UNTP. In this example, we look at the Custom’s officer as the verifier. The officer scans the data carrier on the shipment. UNTP’s practical solution to this is to just return a list of links, and let the verifier “gather” all the documents individually from their origin:
The verifier scans the product’s Data Carrier.
The response is a set of links to where the various documents are hosted.
From these links, the verifier fetches all data for constructing the full data graph.
This indirection has the essential, practical advantage that whoever governs the Data Carrier only needs to maintain a register of where data is placed — without having to physically host the data. The documents related to source products along the value chain remain hosted on those organizations’ web servers.
This architecture also allows for the upstream data issuers to protect data access. While good actors have a natural incentive to flaunt positive certificates, there are plenty of situations where data cannot be made completely public. UNTP’s essential data access control principle is that the product itself can carry the data access key. So, along with the link to the document, the verifier would also be provided the access key on the premise that if you hold the product, you should also be given data access.
The same principle also works for data submission, adding additional data to the DPP. This allows for example post-sale repairs or refurbishments to be registered with the product.
Supplier Confidentiality
Not infrequently, actors along a supply chain seek to protect their business, avoiding ending up as a “cut out middleman”. Such disincentives to reveal upstream data breaks the product traceability.
A 3rd Party Attester, bridging the Transparency Graph where data sharing is prevented.
UNTP’s solution to this obstacle is to introduce an 3rd Party Attester role, which is granted access and verifies to the upstream data graph. Putting its reputation on the line, this accountant-like party issues a document summarizing the product’s origin within a given policy. The summary is stripped from supplier details and can be freely shared with downstream parties.
In our clothing case, assuming the fabric producer does not want to reveal its thread suppliers, it would ask the Attester to verify its supplier documentation and sign a document specifying “all thread used in this batch of fabric comes from organic origin, confirmed back the the non-GMO seeds used for all cotton suppliers”.
Example 3rd Party Attester keeping track of organic thread quotas.
Depending on the type of product, there are a number of different chain of custody patterns which the Attester can apply to capture the traceability from input material to output product. In summary:
Identity Preserved can be used when the same identified product is processed.
Segregated can be used when product types are not being mixed, for example organic and non-organic thread.
Mass Balance can be used when the totals of input and output are important, for example confirming that carbon credits are counted only once.
Book-and-Claim, which can be used when a direct certification-to-product cannot be established.
Says Who?
Let us take a step back now and reflect on what we gain from applying this UNTP infrastructure. How is this any better than, say, icons printed on product boxes? How does it prevent greenwashing?
It all boils down to “says who”. A manufacturer will generally never have the proper incentive structure to make claims about its own products. The UNTP infrastructure and the digital documents we have described are designed to express business variations of express claims from properly incentivised, trustworthy 3rd parties. “Don’t trust my claim of organic origin, trust the organic inspector”.
The enabling technology to establish these trust relationships is a standard called Verifiable Credentials. All the UNTP documents are designed with the intention to be issued as Verifiable Credential, making each document a cryptographically assured data packet. When the credential is issued, the issuer digitally signs the data; this allows any party reading the credential to detect if the data has been tampered with.
This way, as the product data graph is built out, the various claims are distributed out to trustworthy parties, each with a stake in their own domain.
Wrap Up
With this final section we will close this broad introduction article on UNTP and how it is evolving to meet the needs defined by the pending DPP related regulation from the EC and the growing interest globally.
We have deliberately kept the language here non-technical. We also acknowledge that we have not covered all aspects of the DPP ecosystem; for example, the story we have used does not logically extend to the Refurbisher or Repair roles. This article is also very focused on the UN/CEFACT UNTP effort and does not yet include the other standardization efforts underway on the topic. Finally, it is important to note that UNTP is an emerging specification which we still expect will evolve as real life production implementations take off.
We have covered the history of where the concept and demand for the DPP has come from and walked you through a simple story of the creation of a retail clothing product. We have identified the actors who will be using the DPP (Customs Authority, Consumer, Recycler) the stakeholder roles that are part of value chain (Brand, Manufacturer, Auditors, Identity Anchor) and begun to outline the value each of these roles can derive or extract from this effort.
Icons courtesy of flaticon.com